In a recent blog post I discussed the woes of password management and two tools for making password management easier. However, even with a good password management solution in place, it’s still easier than you think for someone to steal your password and gain access to your online accounts. This is particularly true because many of us are guilty of reusing passwords across different websites, meaning many of our online accounts become vulnerable if just one (usually less secure) account is compromised. One thing you can do to add an extra layer of security to your Google account is to implement 2-Step Verification. This will help prevent access to your Google account even if your password is compromised.
[bctt tweet=”It’s easier than you think for someone to steal your password & access your #Google account. Here’s how to safeguard yourself with 2-Step Verification.” username=”samvardanega”]
About Google 2-Step Verification
What is 2-Step Verification?
2-Step Verification provides a more secure way to confirm your identity when logging into your Google account. In order to login, you need to provide two different pieces of information:
- Something you know – this is your password
- Something you have – this is usually a one-time code or physical security key.
As such, even if an attacker identities the something you know, they cannot access your account unless they also have the something you have.
How does Google 2-Step Verification work?
Whenever you sign in to your Google account, you’ll be asked to enter your password as usual. You’ll then be asked for something else, such as a code sent to your phone via text, voice call, or the mobile app. Or, if you have a physical Security Key, you can insert it into your computer’s USB port.
Does that mean I have to enter the 2-Step Verification code every time I sign in?
The first time you sign in to a device with 2-Step Verification, you can choose not to use it again on that specific device. That means that any future logins on that device will only require your password. However, if your account is used to login on another device, the second step of verification will be needed. This means if your password is compromised, an attacker will not be able to use it to access your account.
What options do I have for receiving the 2-Step Verification code?
The something you have can be delivered to your mobile device via one of the following options:
- Text message: The verification code is sent to your mobile phone via a text message.
- Phone call: Google calls your mobile or landline phone with a verification code.
- Google prompt: A prompt appears on your mobile device and you tap ‘Yes’ to sign in.
- Google Authenticator app: This app generates verification codes, even when your device has no phone or data service. It is available for iOS and Android. You can learn more about the app here.
Another option for 2-Step Verification is to purchase a security key. This is a physical device that is inserted into your computer’s USB port. You can read more about security keys here.
[bctt tweet=”Did you know that there are lots of options for using 2-Step Verification with your #Google account?” username=”samvardanega”]
What happens if I lose my mobile device or don’t have it with me?
After you enable 2-Step Verification on your Google account, you can download or print a series of one-time backup codes. These can be used to access your account if you don’t have access to your mobile device or security key. You can also choose to add a backup phone to your account which can be used to receive codes if yours is not available.
Setting up 2-Step Verification on your Google account
Follow the steps below to setup 2-Step Verification on your Google account.
1. Visit https://myaccount.google.com and login with the account you want to enable the 2-Step Verification on.
2. Locate the Sign-in & security section, then click the Signing in to Google link
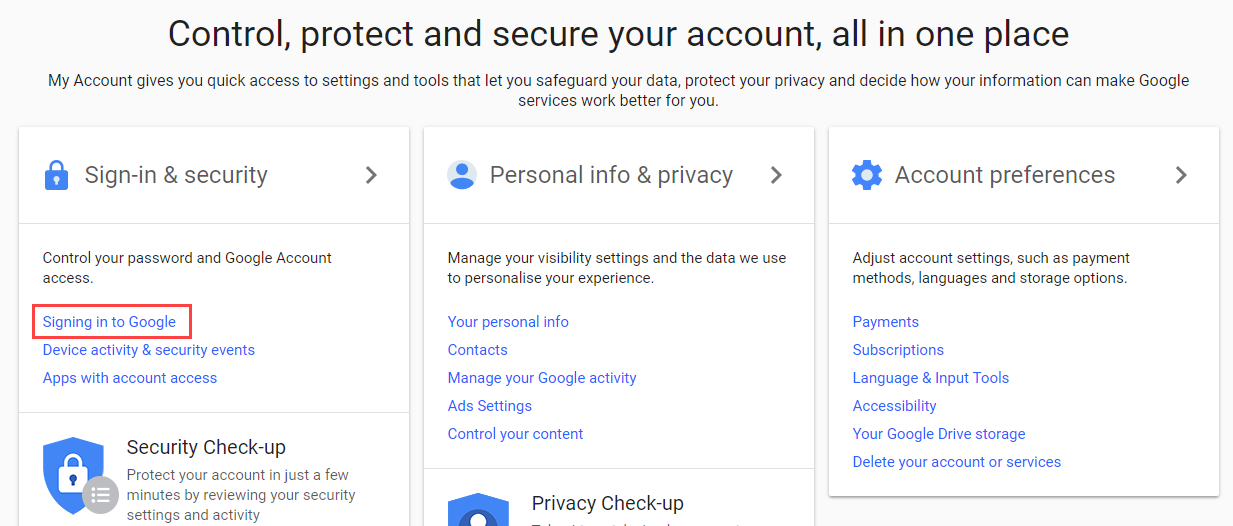
3. Click the 2-Step Verification section.
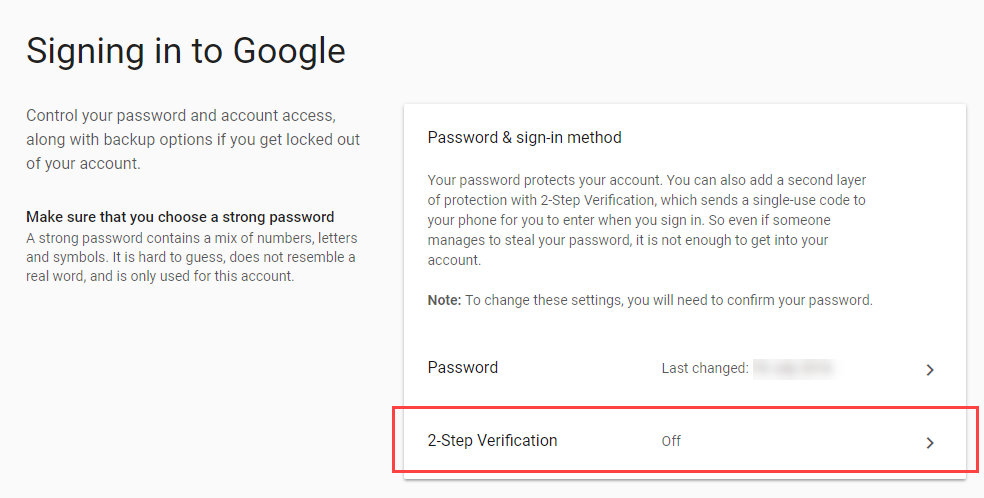
4. Click Get Started and then enter your password when prompted.
5. You will be asked if you want to use a prompt as your second factor for verification. This is a message that will pop-up on your mobile device asking you to tap ‘Yes’.
– If you want to use this method, check the device listed is yours, then click Try it now.
– If you would prefer to use another method, click Don’t use prompt.
Tip: You can easily change your second verification method later too.
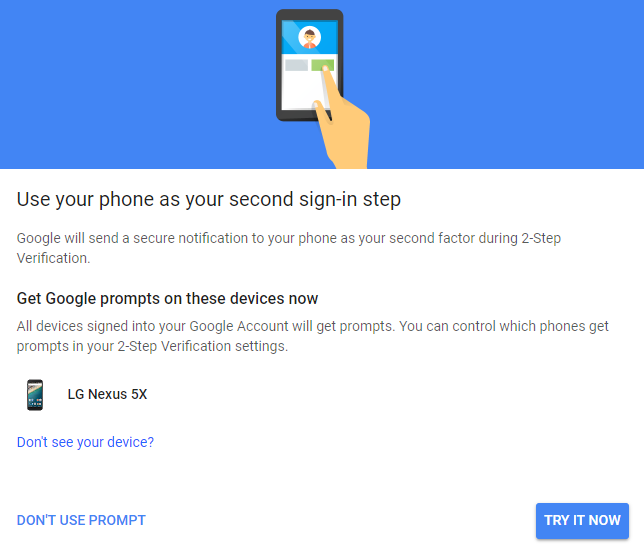
6. If you choose Try it now, a prompt will appear on your mobile device. Tap Yes to confirm the sign-in.
Note: If you did not choose this option, skip ahead to step 7.
7. You will then be asked to choose another verification method, such as a phone number to receive a text message to. Check the number and click Send to send the code.
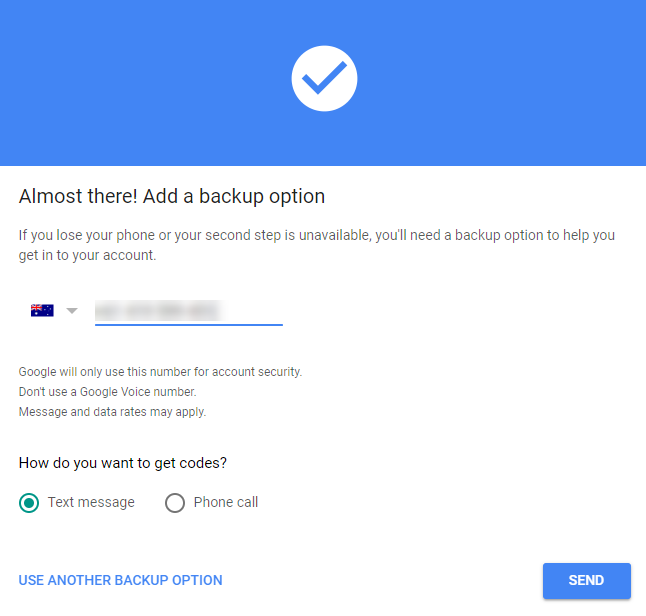
8. Enter the code sent to your device, then click Next.
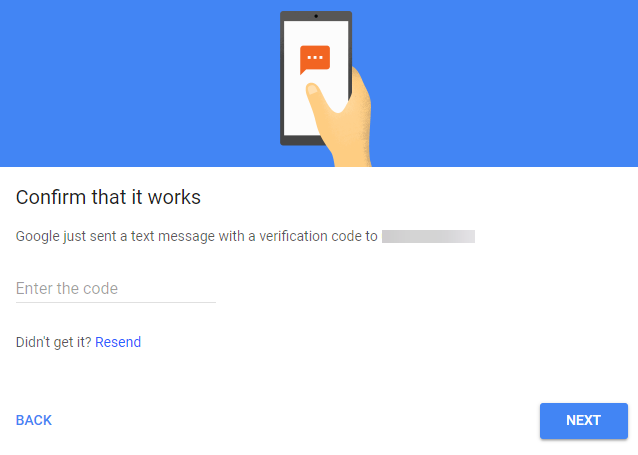
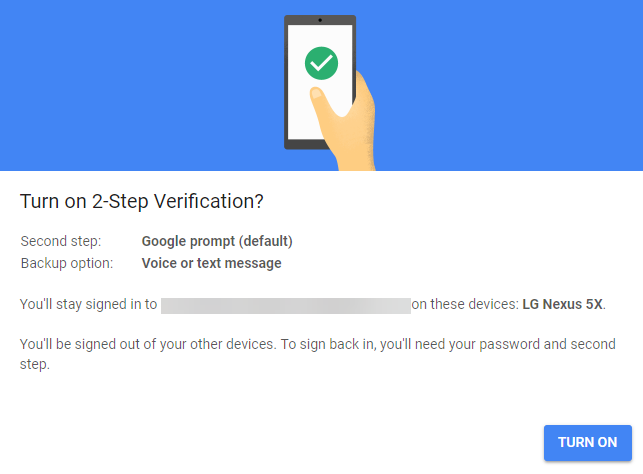
9. Confirm that you want to enable 2-Step Verification by clicking Turn on.
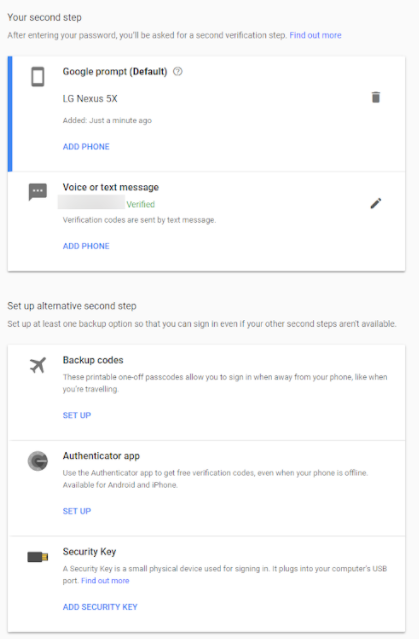
10. You will then be taken to the 2-Step Verification Configuration screen. From here, you can change what you use as your second verification step (including downloading or printing your backup codes) and see the devices that do not need a second step to sign in on.
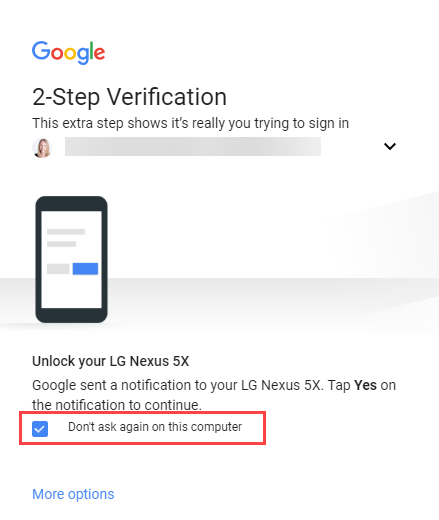
11. The first time you sign into a device using 2-Step Verification, you can choose the option Don’t ask again on this computer if you only want to use your password on that device for future logins.
[bctt tweet=”Here’s how to setup 2-Step Verification on your #Google account and keep your information safe even if your password is compromised” username=”samvardanega”]
If you’re not sure about using 2-Step Verification, sit back and think about all the information you store in your Google account. Would you really want that falling in to the wrong hands? Would you really want someone accessing your account and using it for malicious purposes against your friends and family? If you’ve answered ‘No’ to either of these questions, take a few minutes now to setup 2-Step Verification on all your Google accounts!
If you found this post helpful, you’ll love our online professional learning community, where you get access to Using Technology Better’s training content and expert trainers.
Bonus tip!
If you’re interested in trying out the Google Authenticator app, check out this video on how to set it up.













